Welcome back to the series of Deploying On AWS Cloud Using Terraform 👨🏻💻. In this entire series, we will focus on our core concepts of Terraform by launching important basic services from scratch which will take your infra-as-code journey from beginner to advanced. This series would start from beginner to advance with real-life Usecases and Youtube Tutorials.
If you are a beginner for Terraform and want to start your journey towards infra-as-code developer as part of your DevOps role buckle up 🚴♂️ and let’s get started and understand core Terraform concepts by implementing it…🎬
🔎Basic Terraform Configurations🔍
As part of basic configuration we are going to setup 3 terraform files
1. Providers File:- Terraform relies on plugins called “providers” to interact with cloud providers, SaaS providers, and other APIs.
Providers are distributed separately from Terraform itself, and each provider has its own release cadence and version numbers.
The Terraform Registry is the main directory of publicly available Terraform providers, and hosts providers for most major infrastructure platforms. Each provider has its own documentation, describing its resource types and their arguments.
We would be using AWS Provider for our terraform series. Make sure to refer Terraform AWS documentation for up-to-date information.
Provider documentation in the Registry is versioned; you can use the version menu in the header to change which version you’re viewing.
provider "aws" {
region = "var.AWS_REGION"
shared_credentials_file = ""
}
2. Variables File:- Terraform variables lets us customize aspects of Terraform modules without altering the module’s own source code. This allows us to share modules across different Terraform configurations, reusing same data at multiple places.
When you declare variables in the root terraform module of your configuration, you can set their values using CLI options and environment variables. When you declare them in child modules, the calling module should pass values in the module block.
#-------------------------Data Block to fetch vpc id---------------------
data "aws_vpc" "GetVPC" {
filter {
name = "tag:Name"
values = ["CustomVPC"]
}
}
#-------------------------Variable for RDS Configuration---------------------
variable "rds_instance_identifier" {
type = string
default = "terraform-mysql"
}
variable "db_name" {
type = string
default = "terraform_test_db"
}
variable "db_password" {
type = string
default = ""
}
variable "db_user" {
type = string
default = "terraform"
}
#-------------------------Data Block to fetch subnet ids---------------------
data "aws_subnet_ids" "GetSubnet_Ids" {
vpc_id = data.aws_vpc.GetVPC.id
filter {
name = "tag:Type"
values = ["Public"]
}
}
3. Versions File:- It’s always a best practice to maintain a version file where you specific version based on which your stack is testing and live on production.
terraform {
required_version = ">= 0.12"
}
👨🏻💻Configure Security Group For RDS👨🏻💻
The method acts as a virtual firewall to control your inbound and outbound traffic flowing in and out.
🔳 Resource
✦ aws_security_group:- This resource is define traffic inbound and outbound rules on the subnet level.
🔳 Arguments
✦ name:- This is an optional argument to define the name of the security group.
✦ description:- This is an optional argument to mention details about the security group that we are creating.
✦ vpc_id:- This is a mandatory argument and refers to the id of a VPC to which it would be associated.
✦ tags:- One of the most important property used in all resources. Always make sure to attach tags for all your resources.
EGRESS & INGRESS are processed in attribute-as-blocks mode.
resource "aws_security_group" "rds" {
name = "rds_security_group"
description = "Security group for RDS"
vpc_id = data.aws_vpc.GetVPC.id
# Keep the instance private by only allowing traffic from the web server.
ingress {
from_port = 3306
to_port = 3306
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
# Allow all outbound traffic.
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "rds-security-group"
}
}
👨🏻💻Deploy Database Subnet Group👨🏻💻
🔳 Resource
✦ aws_db_subnet_group:- This resource provides an RDS database subnet group.
🔳 Arguments
✦ name:- This is an optional argument to provide a name to the DB Subnet group instance, if not provided terraform is auto assigns a name.
✦ subnet_ids:- This is a mandatory argument to mention the list of subnet ids under which the RDS instance will be launched.
resource "aws_db_subnet_group" "rds_db_subnet_group" {
name = "rds-subnet-group"
subnet_ids = data.aws_subnet_ids.GetSubnet_Ids.ids
}
👨🏻💻Deploy RDS Instance👨🏻💻
🔳 Resource
✦ aws_db_instance:- This resource is used to launch the RDS instance resource.
🔳 Arguments
✦ identifier:- This is an optional argument to provide a name to the rds instance, if not provided terraform is auto assigns a name.
✦ allocated_storage:- This is a mandatory argument to mention storage allocation in gigabytes.
✦ engine:- This is a mandatory argument to mention the database engine to be used.
✦ engine_version:- This is an optional argument to the specific engine version to be used.
✦ instance_class:- This is a mandatory argument to mention the instance type of RDS instance to be launched.
✦ name :- This is an optional argument to provide a database name to be created after the RDS instance is launched.
✦ username :- This is a mandatory argument to mention the username for the master DB user.
✦ password :- This is a mandatory argument to set a password for the master DB user. Note:- that this may show up in logs, and it will be stored in the state file.
✦ db_subnet_group_name :- This is an optional argument to mention where the DB instance will be created in the VPC associated with the DB subnet group. If unspecified will be created in the default VPC.
✦ vpc_security_group_ids :- This is an optional argument to provide a list of VPC security groups.
✦ skip_final_snapshot:- This option argument to determine whether a final DB snapshot is to be created before the DB instance is deleted. If specified as true, no database snapshot is created. If specified as false, a database snapshot is created before the DB instance is deleted, using the value from final_snapshot_identifier.
✦ final_snapshot_identifier:- This option argument to determine the name of your final Database snapshot when this database instance is deleted. Must be provided if skip_final_snapshot is set to false. The value must begin with a letter, only contain alphanumeric characters and hyphens, and not end with a hyphen or contain two consecutive hyphens.
resource "aws_db_instance" "rds_instance" {
identifier = "${var.rds_instance_identifier}"
allocated_storage = 5
engine = "mysql"
engine_version = "5.6.35"
instance_class = "db.t2.micro"
name = "${var.db_name}"
username = "${var.db_name}"
password = "${var.db_password}"
db_subnet_group_name = "${aws_db_subnet_group.rds_db_subnet_group.id}"
vpc_security_group_ids = ["${aws_security_group.rds.id}"]
skip_final_snapshot = true
final_snapshot_identifier = "Ignore"
}
👨🏻💻Configure parameter group for RDS Instance👨🏻💻
🔳 Resource
✦ aws_db_parameter_group:- This resource creates an RDS parameter group which is a collection of engine configuration values that you set for your RDS database instance.
🔳 Arguments
✦ name:- This is an optional argument to mention the name of the parameter group if not provided terraform will auto-generate a name for it.
✦ description:- This is an optional argument to define descriptive details about the parameter group.
✦ family:-This is a mandatory argument to define family for the parameter group.
Parameter blocks support the following arguments: ✦ name:- This is a mandatory argument to define the name of the database parameter.
✦ value:- This is a mandatory argument to define the value of the database parameter defined in the name.
✦ apply_method:- This option argument to determine whether the parameter should be immediately applicable or after reboot.
resource "aws_db_parameter_group" "rds_para_grp" {
name = "rds-param-group"
description = "Parameter group for mysql5.6"
family = "mysql5.6"
parameter {
name = "character_set_server"
value = "utf8"
}
parameter {
name = "character_set_client"
value = "utf8"
}
}
🔳 Output File
Output values make information about your infrastructure available on the command line, and can expose information for other Terraform configurations to use. Output values are similar to return values in programming languages.
output "aws_db_subnet_group" {
value = aws_db_subnet_group.rds_db_subnet_group.id
description = "This is DB Subnet Group id."
}
output "aws_db_instance" {
value = aws_db_instance.rds_instance.id
description = "This is RDS instance ID."
}
output "aws_db_parameter_group" {
value = aws_db_parameter_group.rds_para_grp.id
description = "This is RDS parameter group ID."
}
🔊To view the entire GitHub code click here
1️⃣ The terraform fmt command is used to rewrite Terraform configuration files to a canonical format and style👨💻.
terraform fmt
2️⃣ Initialize the working directory by running the command below. The initialization includes installing the plugins and providers necessary to work with resources. 👨💻
terraform init
3️⃣ Create an execution plan based on your Terraform configurations. 👨💻
terraform plan
4️⃣ Execute the execution plan that the terraform plan command proposed. 👨💻
terraform apply --auto-approve
👁🗨👁🗨 YouTube Tutorial 📽
❗️❗️Important Documentation❗️❗️
⛔️ Hashicorp Terraform
⛔️ AWS CLI
⛔️ Hashicorp Terraform Extension Guide
⛔️ Terraform Autocomplete Extension Guide
⛔️ AWS Security Group
⛔️ AWS Subnet Group
⛔️ AWS Database Instance
⛔️ AWS DB Parameter Group
🥁🥁 Conclusion 🥁🥁
In this blog, we have configured the below resources
✦ AWS DB subnet group.
✦ AWS Security Group for the RDS Instance.
✦ AWS RDS Instance.
✦ AWS DB Parameter Group.
I have also referenced what arguments and documentation we are going to use so that while you are writing the code it would be easy for you to understand terraform official documentation.
📢 Stay tuned for my next blog…..
So, did you find my content helpful? If you did or like my other content, feel free to buy me a coffee. Thanks.

Author - Dheeraj Choudhary
RELATED ARTICLES
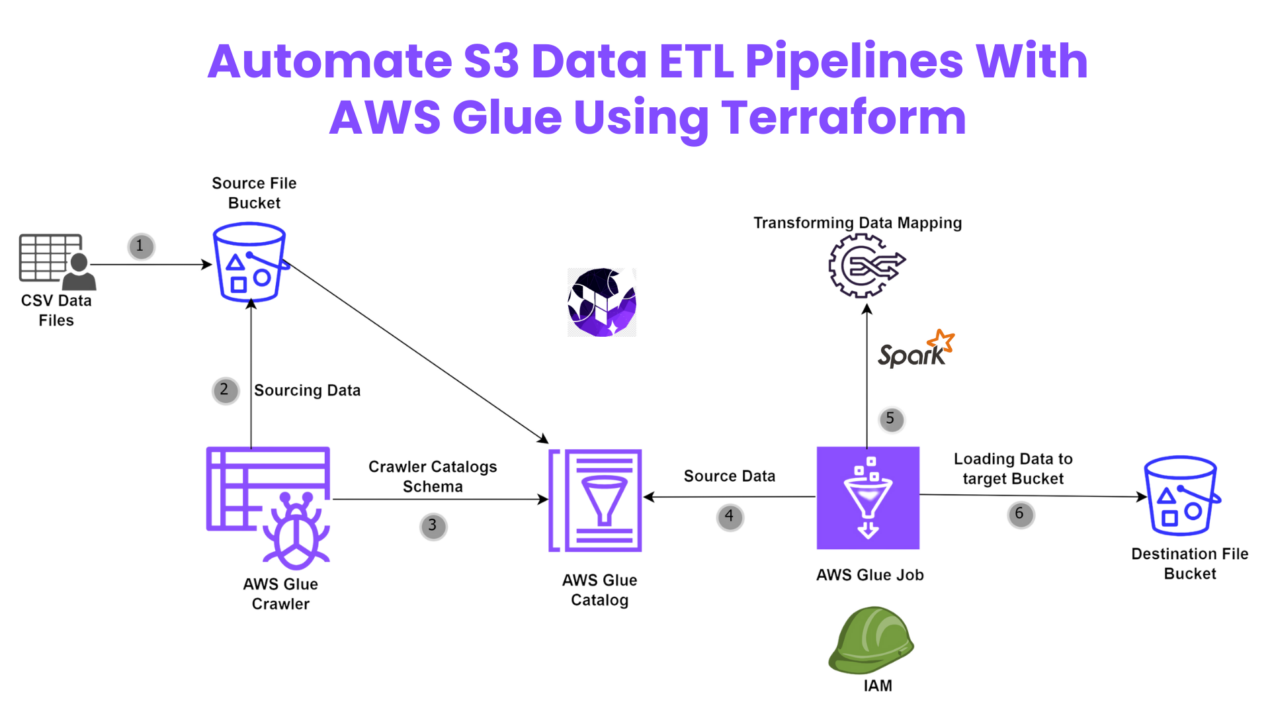
Automate S3 Data ETL Pipelines With AWS Glue Using Terraform
Discover how to automate your S3 data ETL pipelines using AWS Glue and Terraform in this step-by-step tutorial. Learn to efficiently manage and process your data, leveraging the power of AWS Glue for seamless data transformation. Follow along as we demonstrate how to set up Terraform scripts, configure AWS Glue, and automate data workflows.
Automating AWS Infrastructure with Terraform Functions
IntroductionManaging cloud infrastructure can be complex and time-consuming. Terraform, an open-source Infrastructure as Code (IaC) tool, si ...




You actually make it appear really easy together with your presentation but I
in finding this topic to be really something that I think I
would never understand. It sort of feels too complex and very huge for me.
I am looking forward in your subsequent submit, I will
try to get the hold of it! Najlepsze escape roomy
I was reading some of your content on this internet site and
I think this internet site is rattling instructive! Keep on posting.?
I like this site it’s a master piece! Glad I found this ohttps://69v.topn google.Raise your business
I used to be able to find good information from your articles.
Your style is unique in comparison to other folks I’ve read stuff from. Many thanks for posting when you have the opportunity, Guess I will just bookmark this site.
Hello there! I could have sworn I’ve been to your blog before but after looking at a few of the articles I realized it’s new to me. Anyways, I’m definitely delighted I came across it and I’ll be book-marking it and checking back often!
You have made some good points there. I checked on the net for more info about the issue and found most people will go along with your views on this web site.