Welcome back to the series of AWS Cloudformation For Beginners 👨🏻💻. In this blog we will be deploying Public Subnet, Private Subnet & Create Public, Private Route Tables & Associate these route tables to the subnets with help of VS Code Cloudformation Extension.
If you are a beginner and want to start your journey towards infra-as-code developer as part of your devops role buckle up 🚴♂️ and lets get started and understand core cloudformation concepts by implementing it…🎬
🌟Launch Public Subnet, Public Route Table & Associate🌟
Create public subnet, public route table and associate that route table to public subnet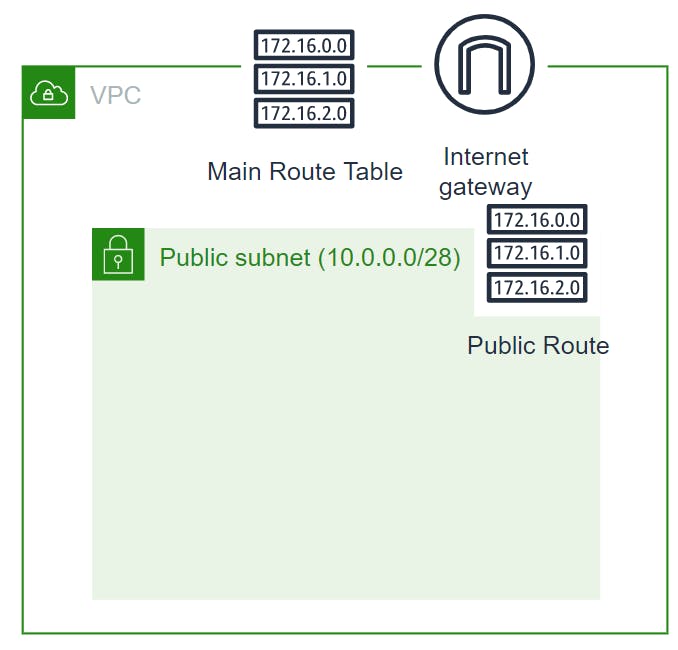 🔳 Parameters:-
🔳 Parameters:-
✦ CustomVPC :- Using this parameter for VPC “AWS::EC2::VPC::Id” we can list existing VPC list into the account and select anyone from them. Apart from this list we can also you default value if no value is selected in the parameter.
✦ CustomInternetGateway :- Using this parameter for Internet gateway with type “String” we are setting default value for this parameter.
🔳 Resources
✦ PublicSubnet:-Specifies a subnet for a VPC. When you create each subnet, you provide the VPC ID and IPv4 CIDR block for the subnet. After you create a subnet, you can’t change its CIDR block. The size of the subnet’s IPv4 CIDR block can be the same as a VPC’s IPv4 CIDR block, or a subset of a VPC’s IPv4 CIDR block.
✦ PublicRouteTable:- Specifies a route table for a specified VPC. After you create a route table, you can add routes and associate the table with a subnet.
✦ PublicRoute:-Specifies a route in a route table within a VPC.You must specify either DestinationCidrBlock or DestinationIpv6CidrBlock, plus the ID of one of the target resources.
✦ PublicSubnetRouteTableAssociation:-Associates a subnet with a route table. The subnet and route table must be in the same VPC. This association causes traffic originating from the subnet to be routed according to the routes in the route table. A route table can be associated with multiple subnets.
🔳 Outputs: Its always a best practice to print output for your resources.
✦ outputVPC: A reference to the created VPC.
✦ outputPublicSubnets: A reference to the created Public subnet.
✦ outputPublicRouteTable: A reference to the created PublicRouteTable.
✦ outputPublicRoute: A reference to the created PublicRoute.
✦ outputPublicSubnetRouteTableAssociation: A reference to the created PublicSubnetRouteTableAssociation.
Parameters:CustomVPC: Description: Select One VPC available in your existing account Type: AWS::EC2::VPC::Id Default: "<Your VPC ID>" CustomInternetGateway: Description: Select One internet gateway available in your existing account Type: String Default: "<Your InternetGateway ID>" Resources: PublicSubnet: Type: AWS::EC2::Subnet Properties: AvailabilityZone: !Select [ 0, !GetAZs '' ] MapPublicIpOnLaunch: true VpcId: !Ref CustomVPC CidrBlock: 10.0.0.0/26 Tags: - Key: Name Value: PublicSubnet PublicRouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: Ref: CustomVPC Tags: - Key: Name Value: PublicRouteTable PublicRoute: # Public route table has direct routing to IGW: Type: AWS::EC2::Route Properties: RouteTableId: !Ref PublicRouteTable DestinationCidrBlock: 0.0.0.0/0 GatewayId: !Ref CustomInternetGateway PublicSubnet1RouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: SubnetId: !Ref PublicSubnet RouteTableId: !Ref PublicRouteTable Outputs: outputVPC: Description: A reference to the created VPC Value: !Ref CustomVPC outputPublicSubnets: Description: Public subnet Value: !Ref PublicSubnet outputPublicRouteTable: Description: A reference to the created PublicRouteTable Value: !Ref PublicRouteTable outputPublicRoute: Description: A reference to the created PublicRoute Value: !Ref PublicRoute outputPublicSubnetRouteTableAssociation: Description: A reference to the created PublicSubnetRouteTableAssociation Value: !Ref PublicSubnetRouteTableAssociation
🔊 To view entire github code click here
1️⃣ Lets validate our template 👨💻
aws cloudformation validate-template --template-body file://<file path>
2️⃣ After successfull template verification lets create stack using our template 👨💻
aws cloudformation create-stack --stack-name launchpublicsubnet --template-body file://<file path>
Note:- If you are not providing default vpc id in parameter then you will have to use below command
aws cloudformation create-stack --stack-name launchpublicsubnet --template-body file://<file path> --parameters ParameterKey=CustomVPC,ParameterValue=<VPC ID>
3️⃣ Check if the stack we created via template is completed successfully 👨💻
aws cloudformation list-stack-resources --stack-name launchpublicsubnet
4️⃣ Describe stack and its resources to view its properties 👨💻
aws cloudformation describe-stacks --stack-name launchpublicsubnet
aws cloudformation describe-stack-resources --stack-name launchpublicsubnet
5️⃣ Check events for stack formation 👨💻
aws cloudformation describe-stack-events --stack-name launchpublicsubnet
👁🗨👁🗨 YouTube Tutorial 📽
🌟Launch Private Subnet, Private Route Table & Associate🌟
Create private subnet, private route table and associate that route table to private subnet.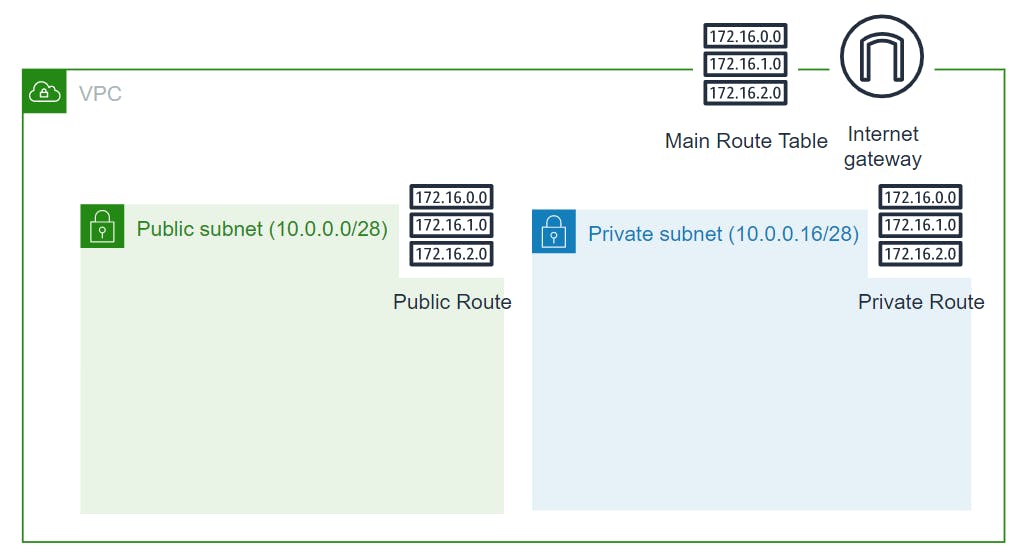 🔳 Parameters:-
🔳 Parameters:-
✦ CustomVPC :- Using this parameter for VPC “AWS::EC2::VPC::Id” we can list existing VPC list into the account and select anyone from them. Apart from this list we can also you default value if no value is selected in the parameter.
🔳 Resources
✦ PrivateSubnet:-Specifies a subnet for a VPC.When you create each subnet, you provide the VPC ID and IPv4 CIDR block for the subnet. After you create a subnet, you can’t change its CIDR block. The size of the subnet’s IPv4 CIDR block can be the same as a VPC’s IPv4 CIDR block, or a subset of a VPC’s IPv4 CIDR block.
✦ PrivateRouteTable:- Specifies a route table for a specified VPC. After you create a route table, you can add routes and associate the table with a subnet.
✦ PrivateSubnetARouteTableAssociation:-Associates a subnet with a route table. The subnet and route table must be in the same VPC. This association causes traffic originating from the subnet to be routed according to the routes in the route table. A route table can be associated with multiple subnets.
🔳 Outputs: Its always a best practice to print output for your resources.
✦ outputVPC: A reference to the created VPC.
✦ outputPrivateSubnets: A reference to the created Private Subnets.
✦ outputPrivateRouteTable: A reference to the created PrivateRouteTable.
✦ outputPrivateSubnetRouteTableAssociation: A reference to the created PrivateSubnetRouteTableAssociation.
Parameters:
CustomVPC:
Description: Select One VPC available in your existing account
Type: AWS::EC2::VPC::Id
Default: <Default VPC ID>
CustomInternetGateway:
Description: Select One internet gateway available in your existing account
Type: String
Default: "igw-0f49c140e9b981dc3"
Resources:
PrivateSubnet:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: !Select [ 0, !GetAZs '' ]
MapPublicIpOnLaunch: true
VpcId: !Ref CustomVPC
CidrBlock: 10.0.0.64/26
Tags:
- Key: Name
Value: PrivateSubnet
PrivateRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref CustomVPC
Tags:
- Key: Name
Value: PrivateRouteTable
PrivateSubnetARouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnet
RouteTableId: !Ref PrivateRouteTable
Outputs:
outputVPC:
Description: A reference to the created VPC
Value: !Ref CustomVPC
outputPrivateSubnets:
Description: A reference to the created Private subnet
Value: !Ref PrivateSubnet
outputPrivateRouteTable:
Description: A reference to the created Private Route Table
Value: !Ref PrivateRouteTable
outputPrivateSubnetRouteTableAssociation:
Description: A reference to the created Private Subnet Route Table Association
Value: !Ref PrivateSubnetARouteTableAssociation
🔊 To view entire github code click here
1️⃣ Lets validate our template 👨💻
aws cloudformation validate-template --template-body file://<file path>
2️⃣ After successfull template verification lets create stack using our template 👨💻
aws cloudformation create-stack --stack-name launchprivatesubnet --template-body file://<file path>
Note:- If you are not providing default vpc id in parameter then you will have to use below command
aws cloudformation create-stack --stack-name launchprivatesubnet --template-body file://<file path> --parameters ParameterKey=CustomVPC,ParameterValue=<VPC ID>
3️⃣ Check if the stack we created via template is completed successfully 👨💻
aws cloudformation list-stack-resources --stack-name launchprivatesubnet
4️⃣ Describe stack and its resources to view its properties 👨💻
aws cloudformation describe-stacks --stack-name launchprivatesubnet
aws cloudformation describe-stack-resources --stack-name launchprivatesubnet
5️⃣ Check events for stack formation 👨💻
aws cloudformation describe-stack-events --stack-name launchprivatesubnet
👁🗨👁🗨 YouTube Tutorial 📽
❗️❗️Important AWS Documentation To Be Viewed❗️❗️
⛔️ AWS::EC2::VPC
⛔️ AWS::EC2::InternetGateway
⛔️ AWS::EC2::Subnet
⛔️ AWS::EC2::RouteTable
⛔️ AWS::EC2::Route
⛔️ AWS::EC2::SubnetRouteTableAssociation
⛔️ Condition functions
⛔️ Managing route tables for your VPC
🥁🥁 Conclusion 🥁🥁
In this blog I have covered 2 usecases in which we will create
✦ Public subnet, public route table and associate that route table to public subnet.
✦ Private subnet, private route table and associate that route table to private subnet.
I have used AWS CLI command to deploy these template and trust me AWS CLI is the realtime hero and I would suggest you to get acquainted towards it. Going forward I will be releasing further parts to this CloudFormation journey
📢 Stay tuned for my next blog…..
So, did you find my content helpful? If you did or like my other content, feel free to buy me a coffee. Thanks

Author - Dheeraj Choudhary
RELATED ARTICLES
Deploy AWS Configuration Along With Security Group And AutoScaling Group Using CloudFormation
Welcome back to the series of AWS Cloudformation For Beginners 👨🏻💻. In this blog we create launch configuration along with security grou ...
Deploy AWS Target Group, Elastic Load Balancer & ELB Listener Using CloudFormation
Welcome back to the series of AWS Cloudformation For Beginners 👨🏻💻. In this blog I am going to deploy resources which are very important ...





1lb5k8
xb961d
Heisy Sanguesa
Tarryn Ziverts
Madelyngrace Rybicka
Very interesting info!Perfect just what I was searching for!Raise range
UDawoRvKZECd
ILUOVydqzZYecmFB
Trishona Iuorno hugo
Nice post! You have written useful and practical information. Take a look at my web blog UY9 I’m sure you’ll find supplementry information about Thai-Massage you can gain new insights from.
7xx9f6