Welcome back to the series of AWS Cloudformation For Beginners 👨🏻💻. In this blog we will be deploying AWS NACL, Inbound & Outbound Routes, Security Group & Associate With Subnet.
If you are a beginner and want to start your journey towards infra-as-code developer as part of your devops role buckle up 🚴♂️ and lets get started and understand core cloudformation concepts by implementing it…🎬
🌟Launch NACL, Inbound & Outbound Routes And Associate With Subnet🌟
Create NACL, NACL Inbound & Outbound Routes And Associate Nacl With Subnet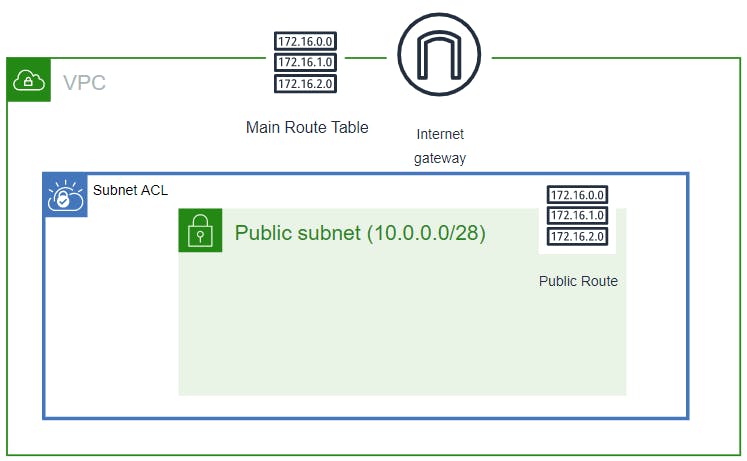 🔳 Parameters:-
🔳 Parameters:-
✦ CustomVPC :- Using this parameter for VPC “AWS::EC2::VPC::Id” we can list existing VPC list into the account and select anyone from them. Apart from this list we can also you default value if no value is selected in the parameter.
✦ PublicSubnet: Using this parameter for Subnet “AWS::EC2::Subnet::Id” we can list existing subnet list from the account and select anyone from them. Apart from this list we can also you default value if no value is selected in the parameter.
🔳 Resources
✦ MyNACL:- As part of this resource we use type “AWS::EC2::NetworkAcl”.
✦ InboundRule & OutboundRule:-. Specifies an entry, known as a rule, in a network ACL with a rule number you specify. Each network ACL has a set of numbered ingress rules and a separate set of numbered egress rules.
✦ mySubnetNetworkAclAssociation:-Associates a subnet with a network ACL.
🔳 Outputs: Its always a best practice to print output for your resources.
✦ outputNACL: A reference to the created NACL.
✦ outputInboundRule: A reference to the created NACL Inbound Rule.
✦ outputEipforNatGateway: A reference to the created EipforNatGateway.
✦ outputNACLOutboundRule: A reference to the created NACL Outbound Rule.
✦ outputNACLSubnetNetworkAclAssociation: A reference to the created NACL Subnet NetworkAcl Association.
Parameters:
CustomVPC:
Description: Select One VPC available in your existing account
Type: AWS::EC2::VPC::Id
Default: "<your default VPC ID>"
PublicSubnet:
Description: Select one public subnet available in your existing account
Type: AWS::EC2::Subnet::Id
Default: "your default public subnet id"
Resources:
MyNACL:
Type: AWS::EC2::NetworkAcl
Properties:
VpcId: !Ref CustomVPC
Tags:
- Key: Name
Value: Nacl
InboundRule:
Type: AWS::EC2::NetworkAclEntry
Properties:
NetworkAclId:
Ref: MyNACL
RuleNumber: 100
Protocol: 6
RuleAction: allow
CidrBlock: 172.16.0.0/24
PortRange:
From: 22
To: 22
OutboundRule:
Type: AWS::EC2::NetworkAclEntry
Properties:
NetworkAclId:
Ref: MyNACL
RuleNumber: 100
Protocol: -1
Egress: true
RuleAction: allow
CidrBlock: 0.0.0.0/0
mySubnetNetworkAclAssociation:
Type: AWS::EC2::SubnetNetworkAclAssociation
Properties:
SubnetId:
Ref: PublicSubnet
NetworkAclId:
Ref: MyNACL
Outputs:
outputNACL:
Description: A reference to the created NACL
Value: !Ref MyNACL
outputInboundRule:
Description: A reference to the created NACL Inbound Rule
Value: !Ref InboundRule
outputNACLOutboundRule:
Description: A reference to the created NACL Outbound Rule
Value: !Ref OutboundRule
outputNACLSubnetNetworkAclAssociation:
Description: A reference to the created NACL Subnet NetworkAcl Association
Value: !Ref mySubnetNetworkAclAssociation
🔊 To view entire github code click here
1️⃣ Lets validate our template 👨💻
aws cloudformation validate-template --template-body file://<file path>
2️⃣ After successfull template verification lets create stack using our template 👨💻
aws cloudformation create-stack --stack-name naclwithsubnetassociation --template-body file://<file path>
Note:- If you are not providing default vpc id in parameter then you will have to use below command
aws cloudformation create-stack --stack-name naclwithsubnetassociation --template-body file://<file path> --parameters ParameterKey=CustomVPC,ParameterValue=<VPC ID>
3️⃣ Check if the stack we created via template is completed successfully 👨💻
aws cloudformation list-stack-resources --stack-name naclwithsubnetassociation
4️⃣ Describe stack and its resources to view its properties 👨💻
aws cloudformation describe-stacks --stack-name naclwithsubnetassociation
aws cloudformation describe-stack-resources --stack-name naclwithsubnetassociation
5️⃣ Check events for stack formation 👨💻
aws cloudformation describe-stack-events --stack-name naclwithsubnetassociation
👁🗨👁🗨 YouTube Tutorial 📽
🌟Deploy Security Group🌟
🔳 Resources
✦ InstanceSecurityGroup:- As part of this resource we use type “AWS::EC2::SecurityGroup”.Specifies a security group. To create a security group, use the VpcId property to specify the VPC for which to create the security group.
🔳 Outputs: Its always a best practice to print output for your resources.
✦ outputInstanceSecurityGroup: A reference to the created security group.
Resources:
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: Enable SSH access and HTTP access on the inbound port
GroupName: AllowAllTraffic
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: 22
ToPort: 22
CidrIp: 0.0.0.0/0
Outputs:
outputInstanceSecurityGroup:
Description: A reference to the created security group
Value: !Ref InstanceSecurityGroup
To view entire github code click here
1️⃣ Lets validate our template 👨💻
aws cloudformation validate-template --template-body file://<file path>
2️⃣ After successfull template verification lets create stack using our template 👨💻
aws cloudformation create-stack --stack-name launchsecuritygroup --template-body file://<file path>
3️⃣ Check if the stack we created via template is completed successfully 👨💻
aws cloudformation list-stack-resources --stack-name launchsecuritygroup
4️⃣ Describe stack and its resources to view its properties 👨💻
aws cloudformation describe-stacks --stack-name launchsecuritygroup
aws cloudformation describe-stack-resources --stack-name launchsecuritygroup
5️⃣ Check events for stack formation 👨💻
aws cloudformation describe-stack-events --stack-name launchsecuritygroup
👁🗨👁🗨 YouTube Tutorial 📽
❗️❗️Important AWS Documentation To Be Viewed❗️❗️
⛔️ AWS::EC2::VPC
⛔️ AWS::EC2::NetworkAcl
⛔️ AWS::EC2::Subnet
⛔️ AWS::EC2::NetworkAclEntry
⛔️ AWS::EC2::SubnetNetworkAclAssociation
⛔️ AWS::EC2::SecurityGroup
⛔️ Condition functions
🥁🥁 Conclusion 🥁🥁
In this blog I have covered 2 scenarios in which we will create
✦ AWS NACL, NACL Inbound & Outbound Routes And Associate Nacl With Subnet
✦ Security Group
I have used AWS CLI command to deploy these template and trust me AWS CLI is the realtime hero and I would suggest you to get acquainted towards it. Stay with me for the next release.
📢 Stay tuned for my next blog…..
So, did you find my content helpful? If you did or like my other content, feel free to buy me a coffee. Thank

Author - Dheeraj Choudhary
RELATED ARTICLES
Deploy AWS Configuration Along With Security Group And AutoScaling Group Using CloudFormation
Welcome back to the series of AWS Cloudformation For Beginners 👨🏻💻. In this blog we create launch configuration along with security grou ...
Deploy AWS Target Group, Elastic Load Balancer & ELB Listener Using CloudFormation
Welcome back to the series of AWS Cloudformation For Beginners 👨🏻💻. In this blog I am going to deploy resources which are very important ...





sexygrannypics.com nude granny is probably not as spry as they used to be, but don’t underestimate grandma’s capability to rock your globe with pleasure! Despite how old they are, they emit confidence and take charge, having an enjoyable experience. Sometimes they’re the ones teaching younger guys something or two and loving every minute of it. Grandmas in adult entertainment fearlessly explore their wishes and beat to fulfill themselves and their partners. Some people might find it a little taboo to speak about this genre. MILF porn is completely fine, but grandma porn? That’s a different story. It’s seen as controversial and not everyone is into it. But hey, if that’s what you’re into, no judgment here! Many individuals enjoy mature adult amusement, so it’s a popular choice for viewers.
Perhaps you have stopped to take into account how old Granny must be feeling? Most of the time, they’re flying solo. Not many pals, and some haven’t any at all. Their own families seem to have forgotten about them, like they weren’t even part of the gang to start with. And in addition, they’ve lost their wife to old age. It’s a pretty rough deal. You’d expect them to possess their friends and family around at that age group, but sadly, they’re all by themselves. No matter how nice and loving they’re, they usually end up alone as they age. It will be great if their loved ones showed them more treatment and attention.
nude granny website : if you’re looking for something spicy and thrilling but bored of the same old, vanilla porn where young porn stars just dive directly into it, then Colombian porn may be the way to go! There’s just something about old porn that continually gets you going. It’s like, anything slightly taboo or forbidden immediately gets people excited, you understand? And there’s this weird excitement in seeing grandmas being sexualized rather than respected. In grandma porn, these ladies are always craving some action.
Naked Grannies Website : Actually consider how older people feel? A lot of the time, they’re all by themselves. Not many friends, and some haven’t any at all. Their own families pretty much left them in the dust, like they weren’t even portion of the family anymore. And in addition, they lost their wife due to later years. It’s a tough circumstance. You’d think they’d have their family and friends around at that age group, but sadly, they’re all by themselves. No matter how kind and loving they are, they usually end up alone because they age. It’d be nice if themselves showed more care and attention.
Hey people!!!!!
Good mood and good luck to everyone!!!!!
Важность строительной экспертизы, Шаги по проведению строительной экспертизы, где найти оптимальные цены, создадут полное понимание, Компетентные специалисты в области строительной экспертизы, готовые помочь вам
Проведение строительной экспертизы требуется для подтверждения соответствия строительных норм. [url=https://www.a-aspect.ru/expertise/stroitelno-tehnicheskie-ekspertizy/stroitelnaya-ekspertiza]https://www.a-aspect.ru/expertise/stroitelno-tehnicheskie-ekspertizy/stroitelnaya-ekspertiza[/url] .
Immerse yourself in a vast array of pictures featuring seductive grandmothers on site HOTGRANNYPORN.COM, properly chosen to fulfill your desires. These mature models, generally within their 50s and old, are really mesmerizing. Witness older ladies engaging in anal sex, delivering mind-blowing blowjobs, and indulging in group sex with genuine satisfaction.
Лучшие сантехники в Сан-Хосе.
Профессиональный сервис сантехников в Сан-Хосе.
Надежные сантехники в Сан-Хосе.
Экстренный вызов сантехника в Сан-Хосе.
Недорогие сантехнические услуги в Сан-Хосе.
Лучшие сантехники для дома в Сан-Хосе.
24 часа в сутки.
Надежные решения для вашей сантехники в Сан-Хосе.
Вызов сантехника в Сан-Хосе.
Экономия на ремонте сантехники в Сан-Хосе.
plumber san jose ca [url=http://www.plumbersan-joseca4.com/]http://www.plumbersan-joseca4.com/[/url] .
Loressa Rostvig
Hey people!!!!!
Good mood and good luck to everyone!!!!!
Encountered and alluring MILFs exude sensuality and confidence, showcasing their knowledge in the artwork of pleasure. From tantalizing poses to intimate acts like anal sex and blowjobs, these females are masters of their craft. Whether dressed up in mesh, tight skirts, or lingerie, they embody the fantasies of an attractive secretary or perhaps a lustful housewife. Our collection features the hottest Milf Busters! Game and cougars in the market, ready to fulfill your wishes. Whether you like shaved or hairy, these seductive versions have something to offer to every flavor. Explore our catalog and enjoy the ultimate experience with these irresistible temptresses.
Latina Tiffany Naked model are usually undeniably a top choice around right here! It’s impossible not to be captivated by way of a seductive ebony goddess like her, her mesmerizing eyes pleading that you should delve deeper into ecstasy. The moment she reveals her adequate natural breasts, your desire will reach new heights. Feel free to spend tribute to these intimate dark porn images. These ebony darlings excel at delivering mind-blowing blowjobs, an art they take great delight in. Discovering the depths of her limited ebony pussy while experiencing the warmth of her mouth area and the sensation of her wet tongue caressing your throbbing member is nothing lacking extraordinary. Remember about her nice, lush ebony pussy and her voluptuous dark derriere, guaranteed to keep you in a state of pure bliss.
Где купить качественный SLS принтер?, как выбрать самый подходящий?.
Какой SLS принтер выбрать из популярных?, преимущества покупки SLS принтера онлайн.
Надежные интернет-магазины с SLS принтерами, сравнение цен на SLS принтеры в разных магазинах.
Советы по выбору и покупке SLS принтера, гарантированный качественный SLS принтер.
Где купить качественный SLS принтер со скидкой?, как выбрать SLS принтер для своих нужд?.
sls принтер купить [url=https://www.slsdd-printer32.ru/]https://www.slsdd-printer32.ru/[/url] .
Лучшие места для покупки промышленного 3D принтера | Что учитывать при покупке промышленного 3D принтера | Преимущества различных промышленных 3D принтеров | Где можно приобрести промышленный 3D принтер | Где найти выгодные цены на промышленные 3D принтеры | Какие бренды промышленных 3D принтеров пользуются популярностью | Какие возможности предоставляют промышленные 3D принтеры | Совместимость материалов с промышленным 3D принтером | За и против приобретения промышленного 3D принтера
промышленные 3d принтеры [url=https://promddd-printer2.ru/]https://promddd-printer2.ru/[/url] .
Какие преимущества у ботокса для волос? – Ботокс для волос улучшает текстуру, увеличивает объем, устраняет пушистость и придает волосам здоровый блеск.
What are the benefits of hair botox? – Hair botox improves texture, increases volume, eliminates frizz, and gives hair a healthy shine.
Через сколько часов можно мыть голову после ботокса для волос [url=http://www.botox.life/articles/skolko-ne-myt-volosy-posle-botoksa]http://www.botox.life/articles/skolko-ne-myt-volosy-posle-botoksa[/url] .
Что вызывает морщины на лбу? – Основные причины включают старение, мимику лица, воздействие ультрафиолета, курение и генетическую предрасположенность.
What causes forehead wrinkles? – The main causes include aging, facial expressions, UV exposure, smoking, and genetic predisposition.
Как избавиться от морщин на лбу с помощью массажа [url=https://www.botox.life/izbavitsya-ot-morshhin-na-lbu]https://www.botox.life/izbavitsya-ot-morshhin-na-lbu[/url] .
Какие показания для применения Ялупро биоревитализанта? – Показания включают сухость кожи, мелкие морщины, фотостарение, снижение тонуса и упругости кожи, а также восстановление после агрессивных косметологических процедур.
What are the indications for using Jalupro Biorevitalizant? – Indications include dry skin, fine wrinkles, photoaging, reduced skin tone and firmness, and recovery after aggressive cosmetic procedures.
Ялупро биоревитализация цена процедуры [url=gmtclinic.ru#Ялупро-биоревитализация-цена-процедуры]gmtclinic.ru[/url] .
Лучшие предложения на 3D принтеры для ювелирного производства, 3D печать для ювелирных изделий, Купите 3D принтер для ювелирных изделий с доставкой, Суперпредложение: 3D печать для ювелиров, Идеальный ювелирный 3D принтер: только лучшие модели, Только у нас вы найдете качественные 3D принтеры для ювелирного дела, Ювелирные 3D принтеры с бесплатной доставкой, Самые надежные 3D принтеры для ювелиров на рынке, Где заказать 3D принтер для ювелирных изделий с гарантией, Выбор ювелиров: 3D печать на заказ, Эффективная 3D печать для ювелиров: все модели в наличии, 3D принтеры для ювелиров: акции и спецпредложения, Выбор ювелира: 3D принтер по доступной цене, Технологии 3D печати для ювелиров: только проверенные модели, Эксклюзивные 3D принтеры для ювелиров: скидки и акции, Где купить высококачественный 3D принтер для ювелиров, Лучшие модели 3D принтеров для ювелиров по акции.
3д принтер ювелирный цена [url=http://printerddd-yuvelirnyj3.ru/]http://printerddd-yuvelirnyj3.ru/[/url] .
Покупайте только лучшие 3д принтеры от отечественного производителя, на всю линейку.
Купить 3д принтер отечественного производства с доставкой по России, со скоростью молнии.
3д принтеры российского производства – надежность и качество, проверено временем.
Получите 3д принтер отечественного производства по лучшей цене, без лишних затрат.
5 причин выбрать 3д принтеры российского производства, о которых вы не знали.
Сертифицированные 3д принтеры отечественного производства, наши рекомендации.
Выбирайте качественные 3д принтеры российского производства, для вашего успеха.
Инновационные 3д принтеры от российских производителей, уже доступны.
3д принтеры российского производства – лучший выбор для вашего бизнеса, для вашего успеха.
3д принтер российского производства купить [url=http://www.rsu-dd3print.ru/]http://www.rsu-dd3print.ru/[/url] .
Как часто нужно посещать частного косметолога? – Частота посещений частного косметолога зависит от состояния кожи и рекомендаций специалиста. Обычно рекомендуется посещать косметолога 1-2 раза в месяц для поддержания здоровья кожи и проведения необходимых процедур. Регулярные визиты помогают своевременно корректировать уход и предотвращать появление кожных проблем.
How often should you visit a private cosmetologist? – The frequency of visits to a private cosmetologist depends on skin condition and specialist recommendations. It is usually recommended to visit a cosmetologist 1-2 times a month to maintain skin health and perform necessary procedures. Regular visits help to timely adjust care and prevent the appearance of skin problems.
Частный косметолог лифтинг [url=https://botox.life/chastnyj-kosmetolog/#Частный-косметолог-лифтинг]Частный косметолог лифтинг[/url] .
Добрый день! Меня зовут Шестаков Юрий Иванович, я дерматолог с многолетним опытом работы в области эстетической медицины. Сейчас я отвечу на ваши вопросы и расскажу полезной информацией о удалении папиллом с помощью лазера. Моя цель — помочь вам понять, как безопасно и эффективно избавиться от папиллом и какие преимущества имеет лазерное удаление.
Какие особенности имеет лазерное удаление папиллом у пожилых людей?
У пожилых людей кожа может быть более чувствительной и склонной к медленному заживлению. При проведении процедуры лазерного удаления папиллом у пожилых пациентов важно учитывать эти особенности и строго следовать рекомендациям врача для минимизации рисков и ускорения процесса заживления.
What are the features of laser removal of papillomas in elderly people?
In elderly people, the skin may be more sensitive and prone to slow healing. When performing laser removal of papillomas in elderly patients, it is important to consider these features and strictly follow the doctor’s recommendations to minimize risks and speed up the healing process.
Какие услуги предоставляет частный косметолог? – Частный косметолог предоставляет широкий спектр услуг, включая чистку лица, химические пилинги, инъекции ботокса и филлеров, лазерные процедуры, уход за кожей и коррекцию возрастных изменений. Дополнительно могут предлагаться такие процедуры, как микродермабразия, мезотерапия, биоревитализация и PRP-терапия. Каждая из этих процедур направлена на улучшение состояния кожи, устранение морщин, акне, пигментации и других кожных проблем.
What services does a private cosmetologist provide? – A private cosmetologist provides a wide range of services including facials, chemical peels, Botox and filler injections, laser treatments, skincare, and correction of age-related changes. Additionally, they may offer procedures like microdermabrasion, mesotherapy, biorevitalization, and PRP therapy. Each of these procedures aims to improve skin condition, eliminate wrinkles, acne, pigmentation, and other skin problems.
Частный косметолог удаление бородавок [url=https://botox.life/chastnyj-kosmetolog/#Частный-косметолог-удаление-бородавок]https://botox.life/chastnyj-kosmetolog/[/url] .
Как выбрать лазерный 3D сканер для профессионального использования, описание основных характеристик.
Выбор профессионалов – лазерные 3D сканеры, широкий выбор.
Купить лазерный 3D сканер легко и выгодно, гарантированный сервис.
Инновационные технологии в сфере лазерных 3D сканеров, полезные советы.
Как выбрать качественный лазерный 3D сканер для дома?, подбор оптимальной модели.
лазерный 3d сканер купить [url=https://lazernyjddd-skaner3.ru/]лазерный 3d сканер купить[/url] .
Передовой промышленный 3D сканер, высокая точность сканирования.
Сравнение различных моделей промышленных 3D сканеров, критерии выбора.
Преимущества использования промышленного 3D сканера, примеры успешного применения.
Основы кибербезопасности для пользователей промышленных 3D сканеров, советы по защите.
Новейшие возможности промышленного 3D сканера, новые горизонты в применении.
3д сканер промышленный [url=http://promyshlennyj3d-skaner6.ru]http://promyshlennyj3d-skaner6.ru[/url] .
RangeVision Pro: новые возможности и функции,
для вашего бизнеса,
RangeVision Pro: высокоточное оборудование для сканирования,
Доверьтесь профессионалам и выберите RangeVision Pro,
RangeVision Pro: максимальная точность и скорость,
Новые возможности с RangeVision Pro,
RangeVision Pro: лучший выбор для профессионалов,
RangeVision Pro: инструмент современного профессионала,
RangeVision Pro: инновации для профессиональных задач,
Выберите RangeVision Pro и ощутите разницу.
сканер rangevision pro [url=range-vision56pro.ru]range-vision56pro.ru[/url] .
Какие преимущества дает использование стоматологических 3D-принтеров|Инновационные методы лечения с помощью 3D-принтеров в стоматологии|Какие критерии отбора нужно учитывать при выборе стоматологического 3D-принтера|Уникальные возможности 3D-печати в стоматологии|Стоматология нового поколения: преимущества 3D-принтеров|Инновационные решения для стоматологических клиник с помощью 3D-принтеров|Почему стоматологические клиники все чаще переходят на использование 3D-принтеров|Что такое биопечать и как она меняет стоматологию|Новые возможности для стоматологии: как принципы 3D-печати меняют отрасль|Новые методы изготовления протезов и конструкций в стоматологии благодаря 3D-принтерам|Инновационные решения для стоматологических клиник с помощью 3D-принтеров|Какие перспективы открывает 3D-печать для стоматологических клиник|3D-принтеры в стоматологии: современные возможности и перспективы|Стоматологические 3D-принтеры: улучшение качества обслуживания пациентов|Какие новые методы лечения появились благодаря стоматологическим 3D-принтерам|Почему стоматологические клиники все чаще переходят на использование 3D-принтеров
3д принтеры для стоматологии купить [url=https://stomatologicheskie34-printery.ru/]3д принтеры для стоматологии купить[/url] .
I like this site it’s a master piece! Glad I found this ohttps://69v.topn google.Raise your business
с Einscan H2 | Подробное руководство по работе с Einscan H2 | Экспертные советы по использованию Einscan H2 | Einscan H2: новые возможности и перспективы | Технические характеристики Einscan H2 | Новый уровень печати на 3D-принтере с Einscan H2 | Секреты оптимизации скорости работы с Einscan H2 | Как повысить эффективность сканирования с Einscan H2 | Подробный обзор стоимости Einscan H2 | Einscan H2: сравнение с конкурентами на рынке | Сравнение функционала Einscan H2 с аналогичными устройствами | Эффективное использование программного обеспечения Einscan H2 | Технологические новшества в Einscan H2 | Инновационные подходы к использованию Einscan H2
einscan h2 [url=nscan3d-h2.ru]nscan3d-h2.ru[/url] .
Узнайте все о 3D-сканере RangeVision Smart, изучите особенности.
Сравните RangeVision Spectrum с другими моделями, примите обоснованное решение.
3D-сканер RangeVision PRO: надежность и качество, забронируйте демонстрацию.
Как выбрать 3D-сканер RangeVision, исходя из ваших целей.
Инновационные решения от RangeVision, познакомьтесь с ассортиментом.
rangevision [url=https://ngevision-rt3.ru]https://ngevision-rt3.ru[/url] .
Indulge in the visual party that is BIG-JUGGS.COM, where each image is carefully crafted to lure and excite. Our own collection showcases gorgeous beauties with typically the most magnificent, jiggliest bosoms you can easily imagine. These temptresses are experts inside the art regarding seduction, flaunting their particular ample cleavage throughout tantalizing poses that will leave you short of breath. Whether they’re caressing, tasting, or merely allowing their adequate assets to hold widely, our lovely girls are here to be able to cater to your every whim and transform your deepest fantasies into happy reality.
Daritza Sutherland
The brunette sensually reveals her beauty in a series of nude photos showcasing women over 50. A milf gracefully enjoys the early morning seashore, swimming naked inside the sea and wandering along the banks. An alluring girl entices her long-haired lover for the passionate encounter in provocative mom adult porn images. The adult cougar indulges in wild sex, your ex trimmed pussy sparkling in solo fleshlight shots. With her engaging eyes hidden powering glasses, a sassy mom inside a short skirt exudes the seductive aura. The slender blonde milf receives a chew of cum right after a steamy blowjob, her mature cunt craving stimulation. A beautiful nude temptress flaunts her hairy pussy in the level of privacy of her dwelling room, arousing wishes with each engaging pose. The skinny milf in white tights exudes a unique sex appeal, her small boobs accentuated in all their glory. The beautiful lady in large heels showcases the woman flexible body within tantalizing porn photos, leaving little to the imagination. The brown-haired beauty in sexy white attire discloses her hairy kitty in provocative photographs old women masturbating loudly, igniting passion in every viewer. This brunette bombshell in a new short skirt and even red lingerie will drive you wild with desire in her amateur photo fixed.
She enjoys the surprise of finding live performances and
acoustic versions when downloading songs from SoundCloud.
Before I download a song from SoundCloud, I check the
comments and reviews to see if other users recommend it.
Marilinda Vocke
Lavare Kurvers
Kyauna Brodhead